21+ Cyber Security O'Reilly Pdf
Hello and welcome to Protocol Entertainment your guide to the business of the gaming and media industries. Together the 27 Members of the College are the Commissions political leadership during a 5-year term.

Cyber Security Report 2021 Pdf Ransomware Phishing
Cyber security teaching approach.
. Gartners newest cybersecurity predictions on third parties quantification and culture. The Institution of Electrical Engineers IEE dating back to 1871 and the Institution of Incorporated Engineers IIE dating back to 1884. White hat hackers break past.
Some intended outcomes could be espionage sabotage propaganda manipulation or economic warfare. Proponents of hacking claim to be motivated by artistic and political ends but are often unconcerned about the use of criminal means to achieve them. They are often connected to a recording device or IP network and may be watched by a security guard or law enforcement officerCameras and recording equipment used to be relatively expensive and required human personnel to monitor camera footage but.
Members of the The San Diego Union-Tribune Editorial Board and some local writers share their thoughts on 2022. Linux is typically packaged as a Linux distribution which includes the kernel and supporting system software and libraries many of which are provided. Integration of security labs with the curriculum in three forms 1 pure virtual 2 traditional physical and 3 hybrid.
Dec 9 2022 202 pm EST. We invite you to share the three favorite things big or small that brought you joy. The CIA triad of confidentiality integrity and availability is at the heart of information security.
Work through 800-171 and CMMC at the same time. 2022 Largest Houston-area cyber security companies. Watch Season 3 Of Our Award-Winning Series Now.
Ad By 2026 50 of cybersecurity leaders will have cybersecurity needs in their contracts. Week of Oct 24 2021. The regions burgeoning cyber security industry has attracted more talent last year but it takes more than just technical knowhow to succeed in the field.
JPMorgan Chase has reached a milestone five years in the making the bank says it is now routing all inquiries from third-party apps and services to access customer data through its secure application programming interface instead of allowing these services to collect data through screen scraping. Networking Technology Companies. Phishing is a type of social engineering where an attacker sends a fraudulent eg spoofed fake or otherwise deceptive message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious software on the victims infrastructure like ransomwarePhishing attacks have become increasingly sophisticated and often transparently.
Ad If you work for the DoD you likely have questions about which regulations youre facing. Teach Your Users Cybersecurity Best Practices To Make Smarter Security Decisions. IT careers and IT skills.
Week of Oct 31 2021. Week of Nov 14 2021. The members of the classic InfoSec triadconfidentiality integrity and availabilityare interchangeably referred to in the literature as security attributes properties security goals fundamental aspects information criteria critical information characteristics and basic building.
Hacker culture is an idea derived from a community of enthusiast computer programmers and systems designers in the 1960s around the Massachusetts Institute of Technologys MITs Tech Model Railroad Club TMRC and the MIT Artificial Intelligence Laboratory. Stay informed and read the latest news today from The Associated Press the definitive source for independent journalism from every corner of the globe. Reverse engineering also known as backwards engineering or back engineering is a process or method through which one attempts to understand through deductive reasoning how a previously made device process system or piece of software accomplishes a task with very little if any insight into exactly how it does so.
Following a bumpy launch week that saw frequent server trouble and bloated player queues Blizzard has announced that over 25 million Overwatch 2 players have logged on in its first 10 daysSinc. New management ideas and research to help thoughtful executives capitalize on the opportunities generated by rapid organizational technological and societal change. Cyberwarfare is the use of cyber attacks against an enemy state causing comparable harm to actual warfare andor disrupting vital computer systems.
In the infancy of the hacker subculture and the computer underground criminal convictions were rare because there was an informal code of ethics that was followed by white hat hackers. Your 1 resource for digital marketing tips trends and strategy to help you build a successful online business. Regulators are leaning toward torpedoing the Activision Blizzard deal.
Week of Nov 21 2021. The term was coined in the 1980s by Barry Collin who discussed this dynamic of terrorism as transcendence from the physical to the virtual realm and the intersection the convergence of these two worlds 6 The Center for Strategic and International Studies CSIS has defined it as the use of computer network tools to shut down critical national. Windows XP is a major release of Microsofts Windows NT operating systemIt was released to manufacturing on August 24 2001 and later to retail on October 25 2001.
There is significant debate among experts regarding the definition of cyberwarfare and even if such a thing exists. The concept expanded to the hobbyist home computing community focusing on hardware in the late 1970s eg. Bei der Bezeichnung PRISM handelt es sich um ein Apronym mit der Bedeutung Planning tool for Resource Integration Synchronization and Management.
Its worldwide membership is currently in excess of 158000 in 153 countries. It is essentially the process of opening up or. Week of Nov 07 2021.
Meet the tech categories and companies defining cybersecurity in 2021 and beyond. Find in-depth news and hands-on reviews of the latest video games video consoles and accessories. The Commission is composed of the College of Commissioners from 27 EU countries.
Microsoft describes the CMAs concerns as misplaced and says that. Microsoft pleaded for its deal on the day of the Phase 2 decision last month but now the gloves are well and truly off. Havent done a DFARS assessment.
Week of Oct 17 2021. It is a direct upgrade to its predecessors Windows 2000 for high-end and business users and Windows Me for home users available for any devices running Windows NT 40 Windows 98 Windows 2000 and. Deutsch Prisma ist ein seit 2005 existierendes und als Top Secret eingestuftes Programm zur Überwachung und Auswertung elektronischer Medien und elektronisch gespeicherter Daten.
Ad Fake Life Real Consequences. This Friday were taking a look at Microsoft and Sonys increasingly bitter feud over Call of Duty and whether UK. Surveillance cameras or security cameras are video cameras used for the purpose of observing an area.
Ranked by Total revenue 2021. The Institution of Engineering and Technology IET is a multidisciplinary professional engineering institutionThe IET was formed in 2006 from two separate institutions. Linux ˈ l iː n ʊ k s LEE-nuuks or ˈ l ɪ n ʊ k s LIN-uuks is a family of open-source Unix-like operating systems based on the Linux kernel an operating system kernel first released on September 17 1991 by Linus Torvalds.
Ad Explore 14 emerging cybersecurity categories 28 high-momentum startups to watch in 2021.

Home Radar Safari Books Online Conferences Pdf O Reilly Media E Books
The Complete Cybersecurity Bootcamp 2nd Edition Video

10 Best Enterprise Architecture Books Features And Price

Pdf Blockchain Technology And Applications
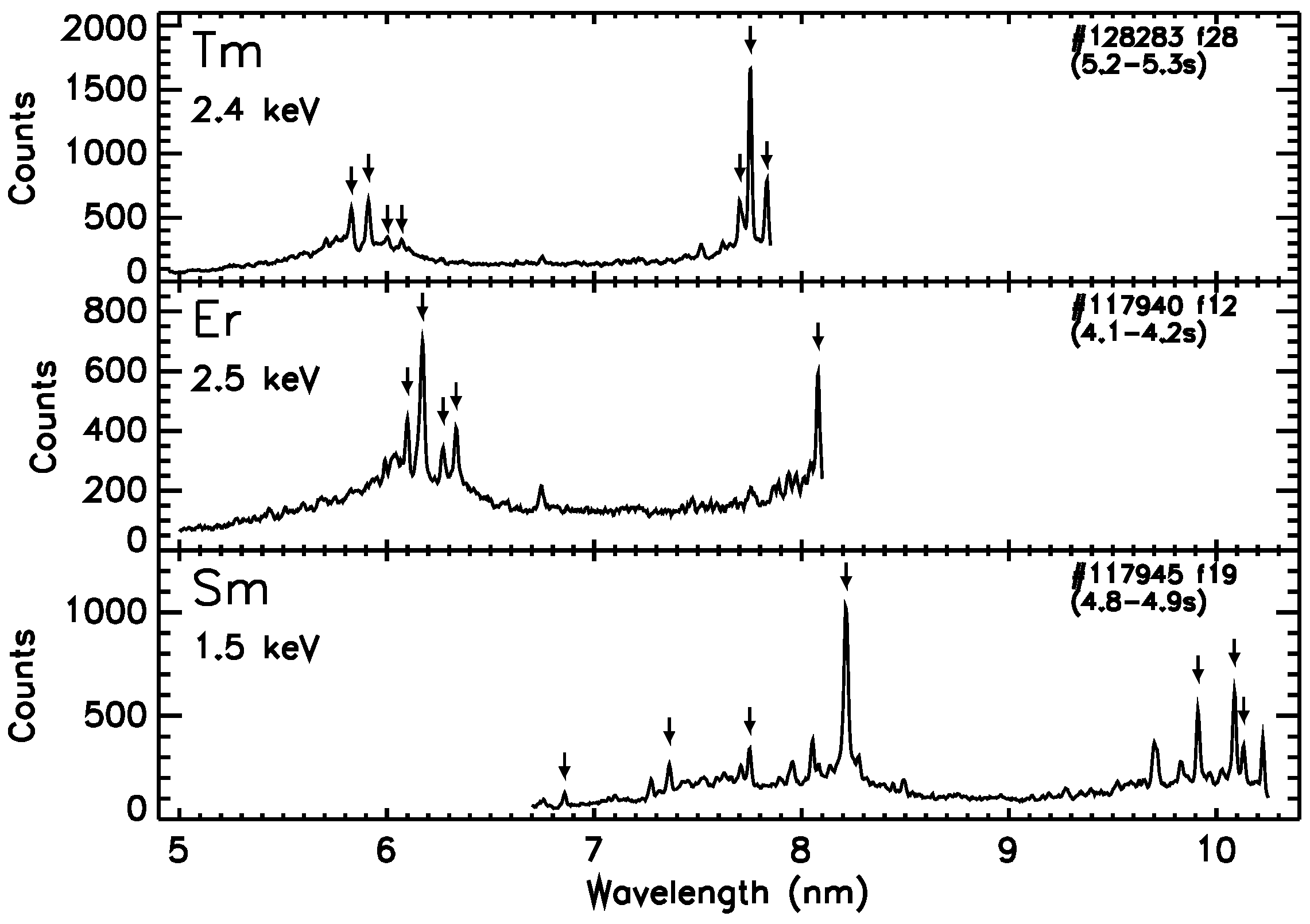
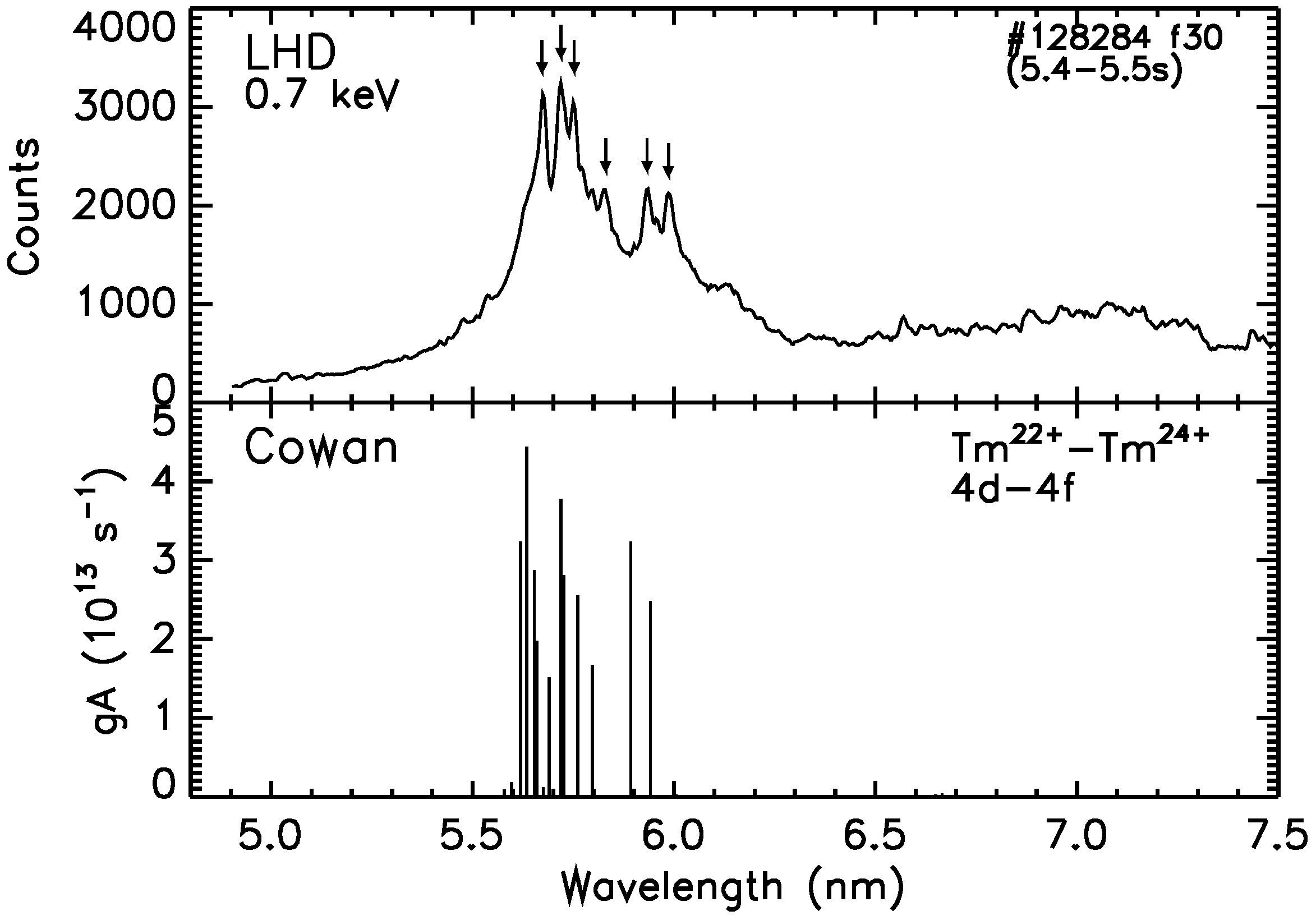
Atoms Free Full Text Soft X Ray Spectroscopy Of Rare Earth Elements In Lhd Plasmas
![]()
Spring Ucsc Extension Silicon Valley

Home Radar Safari Books Online Conferences Pdf O Reilly Media E Books

Pdf Blockchain Technology And Applications
Full Article Occupational Therapy Utilisation Of Apps In Practice In The United States

Cybersecurity 2021 By Carl L Freeman Ebook Scribd

Home Radar Safari Books Online Conferences Pdf O Reilly Media E Books

Pdf Cyber Threats At The Beginning Of The 21st Century
Full Article Restorative Followership In Africa Antecedents Moderators And Consequences

Home Radar Safari Books Online Conferences Pdf O Reilly Media E Books

Education Bergen Resourcenet

Pdf Or Wpsc Aissatou Diallo Academia Edu

Pdf Examining The Development Of The Cyber Marine Ray A Letteer Academia Edu